1. PWN STAR

- Mengelola Antarmuka dan MAC Spoofing
- Mengatur sniffing
- Web phishing
- Karmetasploit
- WPA handshake
- De-auth klien
- Mengelola Iptables
2. ZED ATTACK PROXY (ZAP)

- Intercepting Proxy
- Active scanner
- Passive scanner
- Brute Force scanner
- Spider
- Fuzzer
- Port Scanner
- Dynamic SSL certificates
- API
- Beanshell integration
3. SET (SOCIAL ENGINEERING TOOLKIT)

- Spear-Phishing Attack Vector
- Java Applet Attack Vector
- Metasploit Browser Exploit Method
- Credential Harvester Attack Method
- Tabnabbing Attack Method
- Man Left in the Middle Attack Method
- Web Jacking Attack Method
- Multi-Attack Web Vector
- Infectious Media Generator
- Teensy USB HID Attack Vector
4. BURP SUITE
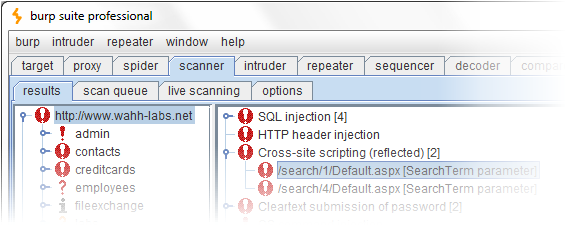
- Intersepsi proxy
- Radar crawling dan spider
- Webapps scanner
- Alat penyerangan
- Repeater dan sequencer tools
5. ETTERCAP
- Untuk melakukan capture traffic dan data
- Untuk melakukan logging network
- Dll
6. SANS INVESTIGATIVE FORENSIC TOOLKIT (SIFT)

- iPhone, Blackberry, and Android Forensic Capabilities
- Registry Viewer (YARU)
- Compatibility with F-Response Tactical, Standard, and Enterprise
- PTK 2.0 (Special Release – Not Available for Download)
- Automated Timeline Generation via log2timeline
- Many Firefox Investigative Plugins
- Windows Journal Parser and Shellbags Parser (jp and sbag)
- Many Windows Analysis Utilities (prefetch, usbstor, event log, and more)
- Complete Overhaul of Regripper Plugins (added over 80 additional plugins)
7. WIRESHARK
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP analysis
- Read/write many different capture file formats
- Dll
8. WEBSPLOIT
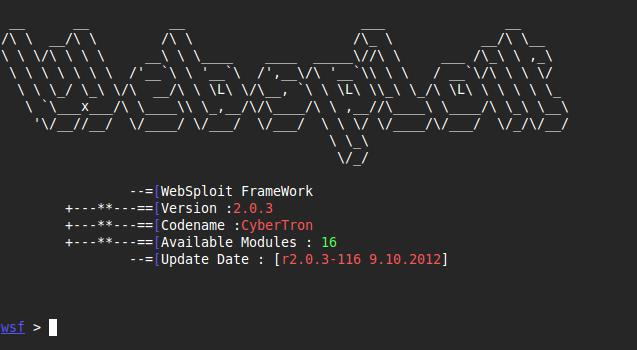
[>]Social Engineering Works
[>]Scan,Crawler & Analysis Web
[>]Automatic Exploiter
[>]Support Network Attacks
—-
[+]Autopwn – Used From Metasploit For Scan and Exploit Target Service
[+]wmap – Scan,Crawler Target Used From Metasploit wmap plugin
[+]format infector – inject reverse & bind payload into file format
[+]phpmyadmin Scanner
[+]LFI Bypasser
[+]Apache Users Scanner
[+]Dir Bruter
[+]admin finder
[+]MLITM Attack – Man Left In The Middle, XSS Phishing Attacks
[+]MITM – Man In The Middle Attack
[+]Java Applet Attack
[+]MFOD Attack Vector
[+]USB Infection Attack
[+]ARP Dos Attack
[+]Web Killer Attack
[+]Fake Update Attack
[+]Fake Access point Attack
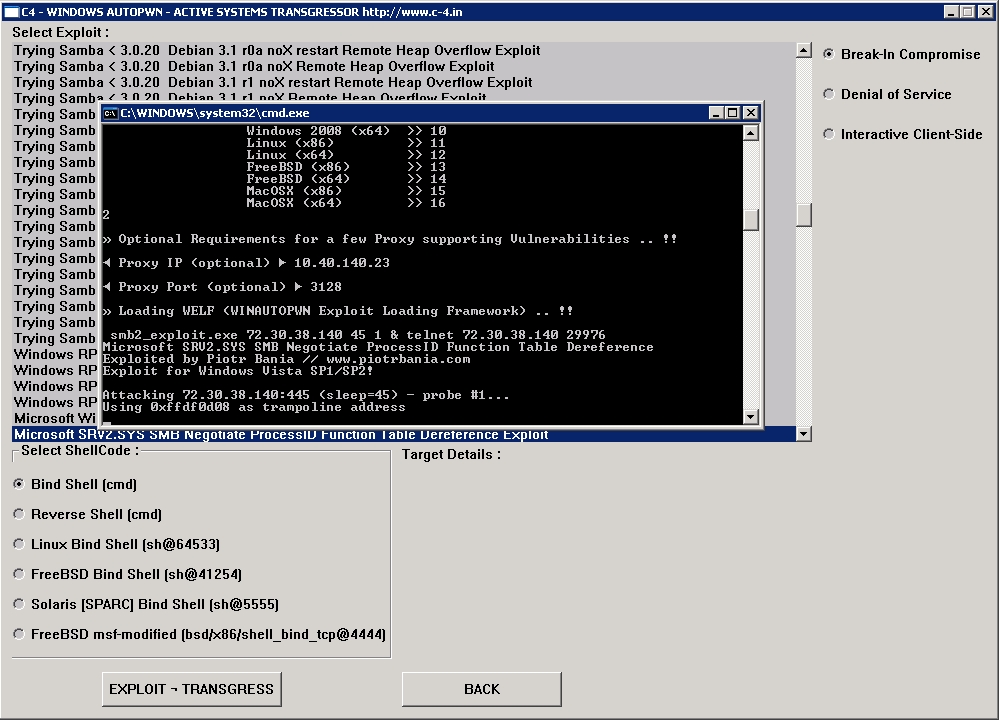
9. WINAUTOPWN
10. HASHCAT
Fungsi Umum:
- Multi-Threaded
- Free
- Multi-Hash (up to 24 million hashes)
- Multi-OS (Linux, Windows and OSX native binaries)
- Multi-Algo (MD4, MD5, SHA1, DCC, NTLM, MySQL, …)
- SSE2 accelerated
- All Attack-Modes except Brute-Force and Permutation can be extended by rules
- Very fast Rule-engine
- Rules compatible with JTR and PasswordsPro
- Possible to resume or limit session
- Automatically recognizes recovered hashes from outfile at startup
- Can automatically generate random rules
- Load saltlist from external file and then use them in a Brute-Force Attack variant
- Able to work in an distributed environment
- Specify multiple wordlists or multiple directories of wordlists
- Number of threads can be configured
- Threads run on lowest priority
- 30+ Algorithms implemented with performance in mind
- … and much more
11. UNISCAN
- Identification of system pages through a Web Crawler.
- Use of threads in the crawler.
- Control the maximum number of requests the crawler.
- Control of variation of system pages identified by Web Crawler.
- Control of file extensions that are ignored.
- Test of pages found via the GET method.
- Test the forms found via the POST method.
- Support for SSL requests (HTTPS).
- Proxy support.
- Generate site list using Google.
- Generate site list using Bing.
- Plug-in support for Crawler.
- Plug-in support for dynamic tests.
- Plug-in support for static tests.
- Plug-in support for stress tests.
- Multi-language support.
- Web client.
12. OLYYDBG
- Intuitive user interface, no cryptical commands
- Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
- Directly loads and debugs DLLs
- Object file scanning – locates routines from object files and libraries
- Allows for user-defined labels, comments and function descriptions
- Understands debugging information in Borland® format
- Saves patches between sessions, writes them back to executable file and updates fixups
- Open architecture – many third-party plugins are available
- No installation – no trash in registry or system directories
- Debugs multithread applications
- Attaches to running programs
- Configurable disassembler, supports both MASM and IDEAL formats
- MMX, 3DNow! and SSE data types and instructions, including Athlon extensions
- Full UNICODE support
- Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
- Recognizes complex code constructs, like call to jump to procedure
- Decodes calls to more than 1900 standard API and 400 C functions
- Gives context-sensitive help on API functions from external help file
- Sets conditional, logging, memory and hardware breakpoints
- Traces program execution, logs arguments of known functions
- Shows fixups
- Dynamically traces stack frames
- Searches for imprecise commands and masked binary sequences
- Searches whole allocated memory
- Finds references to constant or address range
- Examines and modifies memory, sets breakpoints and pauses program on-the-fly
- Assembles commands into the shortest binary form
- Starts from the floppy disk
13. BBQSQL

- SQL Injection Tools
- URL
- HTTP Method
- Headers
- Cookies
- Encoding methods
- Redirect behavior
- Files
- HTTP Auth
- Proxies
14. CRYPTOHAZE

- Crack berbagai macam hash
- Menampilkan hasil dari crackhash
- Cracking di berbagai platform OS
15. SAMURAI WEB TESTING FRAMEWORK (SWTF)

- Web Scanner
- Web Mapping
- Web Exploitation






 9:15:00 AM
9:15:00 AM








